Viewed by a VC investor: Cloud native security (Part 2)
This article depicts the cloud native security market. It belongs to a two-article series on cloud native, where the first one was an introduction to cloud native.
Hi guys, this is Maël from Orange Ventures. Startin’ is a newsletter that aims to share quality content useful for the startup ecosystem (VCs, startups, fundraisers, etc.) regarding new technologies, investments, financial models, etc.
☁️ Cloud native is great! No one would argue it. With it, developers are no more stuck to the build. They can deploy their apps easily and fast. This why, we now count about 6.5 million cloud native developers around the globe.
This fame is highly fuelled by the DevOps trend that is a new way of working to improve collaboration and productivity between developers and operations teams. Both have discrepant objectives: developers are trying to act fast to decrease the time to market while operations are trying to guarantee system stability through time-consuming controls. The aim of cloud native and DevOps is to lead developers & operations teams toward the same goal: Ship bug-free, compliant to any relevant regulations and secured by design apps fast. If you want to better understand cloud native and have some insights regarding this market, go read the first of this two-article series.
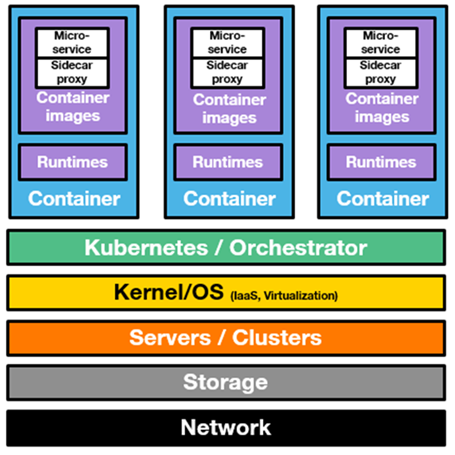
🔒 Protecting cloud native apps is therefore critical. Especially when we estimate that there were about 1.5k data breaches in 2019 according to Statista. Coupled with the 700% increase in the number of enterprise users connecting remotely due to COVID-19, we immediately understand the importance of securing the cloud native stack. This stack is composed of all the elements described below and every single part of it should be protected.
Lost in this stack? If so, go read the previous article of this edition on cloud native that will help you get a clear understanding of it. The promise of cloud native security is to allow developers to use cloud native tools while improving the level of security.
In order to confidently deepdive in the cloud native security market, it is important to first explain the 3 main elements of it that are CASB, infrastructure security and container security.
🔍 The 3 sub-segments of cloud native security
1️⃣ CASB
CASB is an acronym that means Cloud Access Security Broker. Wikipedia defines it as a software that sits between cloud service users and cloud applications, and monitors all activity and enforces security policies. A CASB can offer a variety of services such as monitoring user activity, warning administrators about potentially hazardous actions, enforcing security policy compliance, and automatically preventing malware.
The chart below is helpful to understand how it works and why it is useful.
The CASB market is a mature one, driven by big players that have raised large equity rounds. Among them we find Netskope ($740m raised to date, Series G), or also Bitglass ($150m raised to date, Series D). The main players are based in the US and Israel. These companies are backed by worldwide Tier-1 VCs such as Sequoia Capital, Accel, etc. Recent exits on this market include Orkus acqired by SailPoint (10.2019), or also SkyFormation by Exabeam (07.2019).
2️⃣ Container security
Certainly the most promising sub-segment, container security consists in securing the top part of the cloud native stack presented above. Container security can be seen as a market on its own with several sub-segments. Indeed, there is no company securing the whole container stack at once. To protect it, you must use several complementary solutions. Container security can therefore be split into 6 different parts. Some startups focus on one specific element whereas the majority of them is trying to cover many of them at once. The main 6 elements are the following ones.
Verify images: Containers are created out of layers of files, called container images. It is crucial to verify that the container images signed and from trusted sources
Check the container runtime: The runtimes launch and manage containers. Therefore, it is crucial to closely track the runtime's security patches. Old runtime programs may contain security holes.
Manage access: Private registries allow to control access through role-based assignments while helping manage content by assigning metadata to the container. Metadata identifies and tracks known vulnerabilities. Private registries allow to automate and assign policies for the container images stored.
Integrate security testing and automate deployment: It is crucial to automate policies to flag builds with security issues, especially as new security vulnerabilities are found. As rebuilding containers is better than patching them, integrating security testing should take into account policies that trigger automated rebuilds.
Defend the infrastructure: It is crucial to have a host OS that provides maximum container isolation.
Lock down the operating system: The smaller the operating system, the smaller your attack surface. By reducing the OS installed components to only those needed by the containers, you make it much harder for an attacker to be successful.
Many open source projects, backed by the CNCF community, are operating on the container security market. However, most of them are focusing on the code checking part.
For now, there is still no big players leading this market and most of interesting players are currently between Series A and C. The main last VC deals on this market include the $62m Series C of Aqua Security, the $20m Series A of Anchore, or also the $14m Series A of Styra. As for the famous recent exits, they include the acquisitions of Aporeto (for $150m) and Twistlock (for $410m) by Palo Alto Networks in 2019.
3️⃣ Infrastructure security
The goal of infrastructure security is to deal with the following 3 main risk factors:
Ensuring the confidentiality and integrity of organization’s data-in-transit to and from a public cloud provider.
Ensuring proper access control (authentication, authorization, & auditing) to whatever resources are used at the public cloud.
Ensuring the availability of the Internet-facing resources in a public cloud that are being used by an organization.
This market is also a mature one, led by large public corporations and late stage startups. 70% of the players on this market are based in the USA according to Tracxn. Recent VC deals on the infrastructure security market include the $75M Series F of BetterCloud (01.2020), the $60m Series C of Guardicore (05.2019) or also the $42m Series C of Lacework (09.2019). As for the exits, the last two ones were Cloudvisory acquired by FireEye (01.2020) and 5nine Software acquired by Acronis (12.2019).
💻 Cloud native security market
The cloud native security market is a large growing one. Indeed, according to MarketsandMarkets, it is expected to grow from $34.5B in 2020 to $68.5B in 2025 at a CAGR of 14.7% during the forecasted period. Most players are based in the USA and Israel, similarly to other cybersecurity companies. This market is driven by the following two elements:
Increase in the number of sophisticated cyber-attacks on cloud computing systems, accelerated with the BYOD (Bring Your Own Device) movement and COVID-19 ;
Growing need for compliance with various upcoming regulations.
💵 Deals on the cloud native security market
Cloud native security is so important for developers that Tier-1 VCs have decided to pour millions of dollars on this market in the hope of high returns. Below is a list of the main investors on this market per stage, extracted from Tracxn.
🗺️ Market mapping
When analyzing a cloud native security startup, it is crucial to understand its offerings. Indeed, some of them sell several elements at the same time, such as CASB and elements of container security. In order to have a good understanding of the competition landscape, it is therefore important to understand every company’s offerings. Getting this kind of understanding is also helpful to know which companies are complementary to ensure a full protection of the cloud native stack.
Now that you have a good understanding of the main 3 sub-categories of this market, I let you enjoy the cloud native security mapping below:
About Orange Ventures
Orange Ventures is a venture fund investing in areas of Orange expertise and beyond: we invest in startups with ambition to imagine, design and develop innovative solutions, disruptive technologies and business models of tomorrow.
With 350m€ assets under management Orange Ventures is in the top 10 corporate ventures in Europe with the investment strategy focused on helping future global tech champions, fostering innovation in the Middle East & Africa and supporting new sustainable and responsible business models.
The fund has set financial objectives in line with VC industry standards, leveraging proximity to the Orange Group as a main differentiator in its proposition to startups.